通过这题学习怎么使用Pwntools爆破程序的正确输入,后续也要看看怎么使用Pwntools和Pintools配合来爆破单字节判断flag的题目。
比赛题目没做出来,因为没有看出来是单字节加密,也许出题人就是想让我们爆破的?
题目描述如下
//In the shadowed corridors of an ancient fortress, a legendary knight once safeguarded a secret so potent that countless contenders have vanished trying to decipher it. Now the seal has cracked, and echoes of its power seep into the present. Test your courage as you follow cryptic traces left by the knight’s hand, unraveling an enigma steeped in the mysticism of ages past. Will your wits prove enough to break the bindings and uncover the realm’s hidden legacy—or will you, too, fade into the swirling mists of history? The choice—and fate—are yours to determine.
//Flag Format : KCTF{s0mething_here}
//Author: Noman Prodhan打开附件给的ELF,拖入IDA,主逻辑实在又臭又长
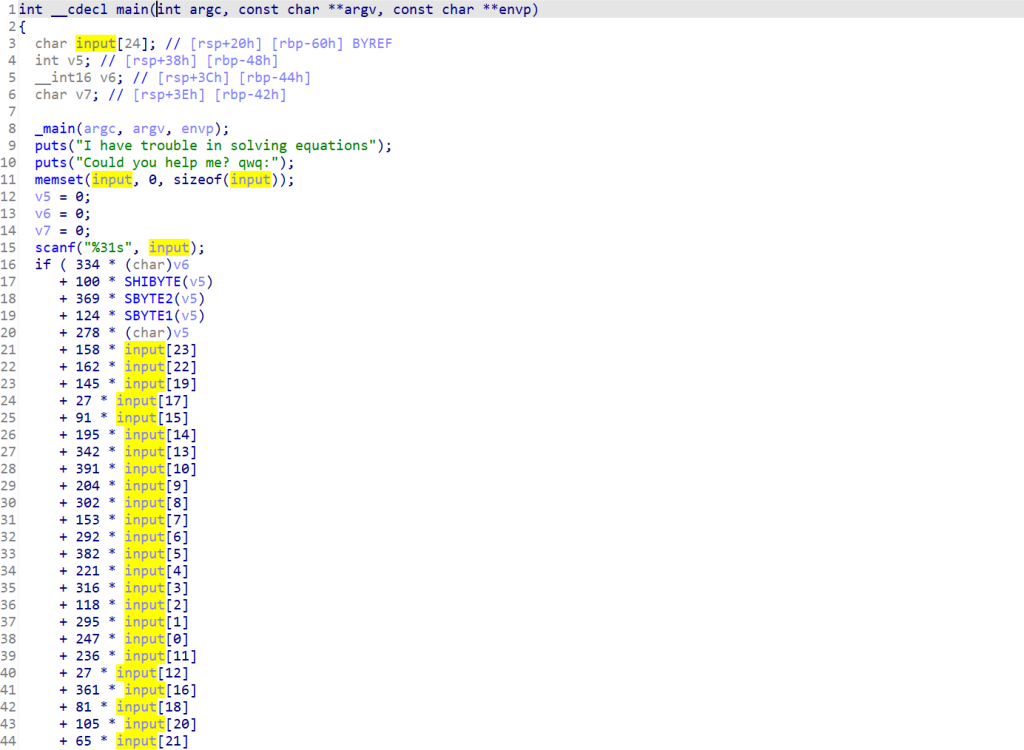
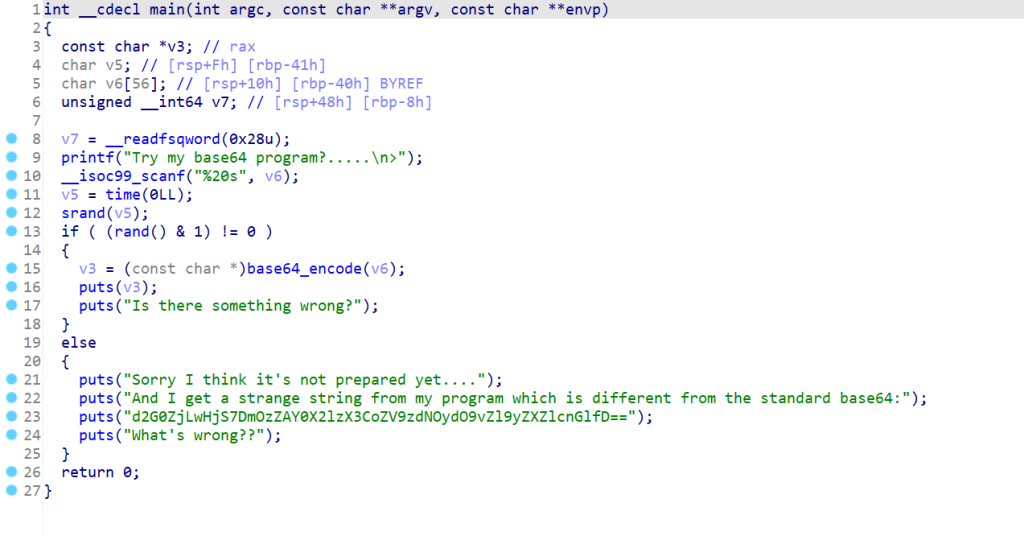
__int64 __fastcall main(int a1, char **a2, char **a3)
{
size_t v3; // rax
const unsigned __int16 *v5; // rcx
__int64 v6; // rax
__m128i v7; // xmm11
__m128i v8; // xmm6
__m128i inserted; // xmm0
__m128i v10; // xmm1
__m128i v11; // xmm3
__m128i v12; // xmm15
__m128i v13; // xmm13
__m128i v14; // xmm14
__m128i v15; // xmm10
unsigned int v16; // edx
__m128i v17; // xmm3
__m128i v18; // xmm4
__m128i v19; // xmm1
__m128i v20; // xmm7
__m128i v21; // xmm0
__m128i v22; // xmm4
__m128i v23; // xmm15
__m128i v24; // xmm7
__m128i v25; // xmm1
__m128i v26; // xmm14
__m128i v27; // xmm10
__m128i v28; // xmm3
__m128i v29; // xmm0
__m128i v30; // xmm4
__m128i v31; // xmm1
__m128i v32; // xmm15
__m128i v33; // xmm12
__m128i v34; // xmm7
__m128i v35; // xmm14
__m128i v36; // xmm12
__m128i v37; // xmm7
__m128i v38; // xmm12
__m128i v39; // xmm10
__m128i v40; // xmm7
__m128i v41; // xmm14
__m128i v42; // xmm7
__m128i v43; // xmm10
__m128i v44; // xmm12
__m128i v45; // xmm10
__m128i v46; // xmm7
__m128i v47; // xmm3
__m128i v48; // xmm10
__m128i v49; // xmm7
__m128i v50; // xmm10
__m128i v51; // xmm7
__m128i v52; // xmm14
__m128i v53; // xmm3
__m128i v54; // xmm7
__m128i v55; // xmm14
__m128i v56; // xmm12
__m128i v57; // xmm7
__m128i v58; // xmm3
__m128i v59; // xmm0
__m128i v60; // xmm7
__m128i v61; // xmm3
__m128i v62; // xmm4
__m128i v63; // xmm3
__m128i v64; // xmm4
__m128i v65; // xmm0
__m128i v66; // xmm4
__m128i v67; // xmm3
__m128i v68; // xmm1
__m128i v69; // xmm4
__m128i v70; // xmm3
__m128i v71; // xmm3
__m128i v72; // xmm4
__m128i v73; // xmm3
__m128i v74; // xmm0
__m128i v75; // xmm1
__m128i v76; // xmm4
__m128i v77; // xmm12
__m128i v78; // xmm1
__m128i v79; // xmm1
__m128i v80; // xmm2
__m128i v81; // xmm0
__m128i v82; // xmm0
__m128i v83; // xmm0
__m128i v84; // xmm0
__m128i v85; // xmm0
__m128i v86; // xmm0
int v87; // eax
unsigned __int16 v88; // dx
unsigned __int16 v89; // dx
__m128i v90; // [rsp+0h] [rbp-2F8h] BYREF
__m128i v91; // [rsp+10h] [rbp-2E8h] BYREF
__m128i v92; // [rsp+20h] [rbp-2D8h] BYREF
__m128i v93; // [rsp+30h] [rbp-2C8h] BYREF
__m128i v94; // [rsp+40h] [rbp-2B8h] BYREF
__m128i v95; // [rsp+50h] [rbp-2A8h] BYREF
__m128i v96; // [rsp+60h] [rbp-298h] BYREF
__m128i v97; // [rsp+70h] [rbp-288h] BYREF
__m128i v98; // [rsp+80h] [rbp-278h]
__m128i v99; // [rsp+90h] [rbp-268h]
__m128i v100[15]; // [rsp+A0h] [rbp-258h] BYREF
__m128i si128; // [rsp+190h] [rbp-168h]
__int128 s2[2]; // [rsp+1A0h] [rbp-158h] BYREF
__int16 v103; // [rsp+1C0h] [rbp-138h]
char s[32]; // [rsp+1D0h] [rbp-128h] BYREF
unsigned __int8 v106; // [rsp+1F0h] [rbp-108h]
unsigned __int8 v107; // [rsp+1F1h] [rbp-107h]
char s1[136]; // [rsp+250h] [rbp-A8h] BYREF
unsigned __int64 v109; // [rsp+2D8h] [rbp-20h]
v109 = __readfsqword(0x28u);
v103 = 5200;
s2[0] = (__int128)_mm_load_si128((const __m128i *)&xmmword_2060);
s2[1] = (__int128)_mm_load_si128((const __m128i *)&xmmword_2070);
printf("Hello Knight\nEnter your secret: ");
fgets(s, 128, stdin);
v3 = strlen(s);
if ( !v3 )
goto LABEL_5;
if ( s[v3 - 1] == 10 )
s[--v3] = 0;
if ( v3 != 34 )
goto LABEL_5;
v5 = *__ctype_b_loc();
v6 = 0LL;
v95 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0xFFFFFFC0), 0);
v96 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0xFFFFFFA0), 0);
v97 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x1000100u), 0);
v91 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0xFF00FFu), 0);
v7 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x4EC4EC4Fu), 0);
v98 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x41414141u), 0);
v8 = _mm_cmpgt_epi32((__m128i)0LL, v7);
v99 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x61616161u), 0);
v100[0] = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x4000400u), 0);
do
{
si128 = _mm_load_si128((const __m128i *)&s[v6]);
v100[14] = si128;
v100[13] = si128;
v100[12] = si128;
v100[11] = si128;
v100[10] = si128;
v100[9] = si128;
inserted = _mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[4]]), v5[si128.m128i_u8[5]], 1);
v10 = _mm_unpacklo_epi32(
_mm_insert_epi16(_mm_cvtsi32_si128(v5[(unsigned __int8)_mm_cvtsi128_si32(si128)]), v5[si128.m128i_u8[1]], 1),
_mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[2]]), v5[si128.m128i_u8[3]], 1));
v11 = _mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[6]]), v5[si128.m128i_u8[7]], 1);
v100[8] = si128;
v100[7] = si128;
v100[6] = si128;
v100[5] = si128;
v100[4] = si128;
v12 = _mm_load_si128(&v95);
v100[3] = si128;
v13 = _mm_load_si128(&v96);
v14 = v12;
v15 = v12;
v100[2] = si128;
v100[1] = si128;
v16 = v5[si128.m128i_u8[8]];
v92 = _mm_unpacklo_epi64(v10, _mm_unpacklo_epi32(inserted, v11));
v17 = v12;
v93 = _mm_unpacklo_epi64(
_mm_unpacklo_epi32(
_mm_insert_epi16(_mm_cvtsi32_si128(v16), v5[si128.m128i_u8[9]], 1),
_mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[10]]), v5[si128.m128i_u8[11]], 1)),
_mm_unpacklo_epi32(
_mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[12]]), v5[si128.m128i_u8[13]], 1),
_mm_insert_epi16(_mm_cvtsi32_si128(v5[si128.m128i_u8[14]]), v5[si128.m128i_u8[15]], 1)));
v18 = _mm_unpacklo_epi8(si128, (__m128i)0LL);
v19 = _mm_unpackhi_epi8(si128, (__m128i)0LL);
v20 = _mm_unpackhi_epi16(v19, (__m128i)0LL);
v21 = _mm_unpacklo_epi16(v18, (__m128i)0LL);
v22 = _mm_unpackhi_epi16(v18, (__m128i)0LL);
v90 = _mm_add_epi32(v12, v20);
v23 = v20;
v24 = _mm_load_si128(&v97);
v25 = _mm_unpacklo_epi16(v19, (__m128i)0LL);
v26 = _mm_add_epi32(v14, v21);
v27 = _mm_add_epi32(v15, v22);
v28 = _mm_add_epi32(v17, v25);
v29 = _mm_add_epi32(v21, v13);
v30 = _mm_add_epi32(v22, v13);
v31 = _mm_add_epi32(v25, v13);
v32 = _mm_add_epi32(v23, v13);
v94 = _mm_packus_epi16(
_mm_and_si128(
_mm_cmpeq_epi16(_mm_cmpeq_epi16(_mm_and_si128(v24, v92), (__m128i)0LL), (__m128i)0LL),
_mm_load_si128(&v91)),
_mm_and_si128(_mm_cmpeq_epi16(_mm_cmpeq_epi16(_mm_and_si128(v24, v93), (__m128i)0LL), (__m128i)0LL), v91));
v33 = _mm_srli_epi64(v26, 0x20u);
v34 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v26, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v26), v7),
_mm_mul_epu32(v8, v26)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v33, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v33), v7),
_mm_mul_epu32(v8, v33)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v26, 0x1Fu));
v35 = _mm_sub_epi32(
v26,
_mm_slli_epi32(_mm_add_epi32(v34, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v34, 1u), v34), 2u)), 1u));
v36 = _mm_srli_epi64(v27, 0x20u);
v37 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v27, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v27), v7),
_mm_mul_epu32(v8, v27)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v36, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v36), v7),
_mm_mul_epu32(v8, v36)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v27, 0x1Fu));
v38 = v35;
v39 = _mm_sub_epi32(
v27,
_mm_slli_epi32(_mm_add_epi32(v37, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v37, 1u), v37), 2u)), 1u));
v40 = v35;
v41 = _mm_load_si128(&v90);
v42 = _mm_unpackhi_epi16(v40, v39);
v43 = _mm_unpacklo_epi16(v38, v39);
v44 = _mm_unpacklo_epi16(_mm_unpacklo_epi16(v43, v42), _mm_unpackhi_epi16(v43, v42));
v45 = _mm_srli_epi64(v28, 0x20u);
v46 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v28, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v28), v7),
_mm_mul_epu32(v8, v28)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v45, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v45), v7),
_mm_mul_epu32(v8, v45)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v28, 0x1Fu));
v47 = _mm_sub_epi32(
v28,
_mm_slli_epi32(_mm_add_epi32(v46, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v46, 1u), v46), 2u)), 1u));
v48 = _mm_srli_epi64(v41, 0x20u);
v49 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v41, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v41), v7),
_mm_mul_epu32(v8, v41)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v48, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v48), v7),
_mm_mul_epu32(v8, v48)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v41, 0x1Fu));
v50 = _mm_add_epi32(_mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v49, 1u), v49), 2u), v49);
v51 = v47;
v52 = _mm_sub_epi32(v41, _mm_slli_epi32(v50, 1u));
v53 = _mm_unpacklo_epi16(v47, v52);
v54 = _mm_unpackhi_epi16(v51, v52);
v55 = _mm_load_si128(&v91);
v56 = _mm_add_epi8(
_mm_packus_epi16(
_mm_and_si128(v44, v55),
_mm_and_si128(_mm_unpacklo_epi16(_mm_unpacklo_epi16(v53, v54), _mm_unpackhi_epi16(v53, v54)), v55)),
v98);
v57 = _mm_srli_epi64(v29, 0x20u);
v58 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v29, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v29), v7),
_mm_mul_epu32(v8, v29)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v57, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v57), v7),
_mm_mul_epu32(v8, v57)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v29, 0x1Fu));
v59 = _mm_sub_epi32(
v29,
_mm_slli_epi32(_mm_add_epi32(v58, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v58, 1u), v58), 2u)), 1u));
v60 = _mm_srli_epi64(v30, 0x20u);
v61 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v30, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v30), v7),
_mm_mul_epu32(v8, v30)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v60, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v60), v7),
_mm_mul_epu32(v8, v60)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v30, 0x1Fu));
v62 = _mm_sub_epi32(
v30,
_mm_slli_epi32(_mm_add_epi32(v61, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v61, 1u), v61), 2u)), 1u));
v63 = _mm_unpackhi_epi16(v59, v62);
v64 = _mm_unpacklo_epi16(v59, v62);
v65 = _mm_unpacklo_epi16(_mm_unpacklo_epi16(v64, v63), _mm_unpackhi_epi16(v64, v63));
v66 = _mm_srli_epi64(v31, 0x20u);
v67 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v31, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v31), v7),
_mm_mul_epu32(v8, v31)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v66, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v66), v7),
_mm_mul_epu32(v8, v66)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v31, 0x1Fu));
v68 = _mm_sub_epi32(
v31,
_mm_slli_epi32(_mm_add_epi32(v67, _mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v67, 1u), v67), 2u)), 1u));
v69 = _mm_srli_epi64(v32, 0x20u);
v70 = _mm_sub_epi32(
_mm_srai_epi32(
_mm_shuffle_epi32(
(__m128i)_mm_shuffle_ps(
(__m128)_mm_add_epi64(
_mm_mul_epu32(v32, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v32), v7),
_mm_mul_epu32(v8, v32)),
0x20u)),
(__m128)_mm_add_epi64(
_mm_mul_epu32(v69, v7),
_mm_slli_epi64(
_mm_add_epi64(
_mm_mul_epu32(_mm_cmpgt_epi32((__m128i)0LL, v69), v7),
_mm_mul_epu32(v8, v69)),
0x20u)),
221),
216),
3u),
_mm_srai_epi32(v32, 0x1Fu));
v71 = _mm_sub_epi32(
v32,
_mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(_mm_add_epi32(_mm_slli_epi32(v70, 1u), v70), 2u), v70), 1u));
v72 = _mm_unpackhi_epi16(v68, v71);
v73 = _mm_unpacklo_epi16(v68, v71);
v74 = _mm_add_epi8(
_mm_packus_epi16(
_mm_and_si128(v65, v55),
_mm_and_si128(_mm_unpacklo_epi16(_mm_unpacklo_epi16(v73, v72), _mm_unpackhi_epi16(v73, v72)), v55)),
v99);
v75 = _mm_load_si128(&v94);
v76 = _mm_load_si128(v100);
v77 = _mm_or_si128(_mm_and_si128(v56, v75), _mm_andnot_si128(v75, v74));
v78 = _mm_packus_epi16(
_mm_and_si128(
_mm_cmpeq_epi16(_mm_cmpeq_epi16(_mm_and_si128(_mm_load_si128(&v92), v76), (__m128i)0LL), (__m128i)0LL),
v55),
_mm_and_si128(
_mm_cmpeq_epi16(_mm_cmpeq_epi16(_mm_and_si128(_mm_load_si128(&v93), v76), (__m128i)0LL), (__m128i)0LL),
v55));
v79 = _mm_or_si128(_mm_andnot_si128(v78, si128), _mm_and_si128(v77, v78));
v80 = _mm_shuffle_epi32(_mm_cvtsi32_si128(0x1010101u), 0);
v81 = _mm_or_si128(
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0x7F7F7F7Fu), 0), _mm_srli_epi16(v79, 1u)),
v80),
_mm_and_si128(_mm_add_epi8(v79, v79), _mm_shuffle_epi32(_mm_cvtsi32_si128(0x2020202u), 0)));
v82 = _mm_or_si128(
_mm_add_epi8(v81, v81),
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0x3F3F3F3Fu), 0), _mm_srli_epi16(v79, 2u)),
v80));
v83 = _mm_or_si128(
_mm_add_epi8(v82, v82),
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0x1F1F1F1Fu), 0), _mm_srli_epi16(v79, 3u)),
v80));
v84 = _mm_or_si128(
_mm_add_epi8(v83, v83),
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0xF0F0F0Fu), 0), _mm_srli_epi16(v79, 4u)),
v80));
v85 = _mm_or_si128(
_mm_add_epi8(v84, v84),
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0x7070707u), 0), _mm_srli_epi16(v79, 5u)),
v80));
v86 = _mm_or_si128(
_mm_add_epi8(v85, v85),
_mm_and_si128(
_mm_and_si128(_mm_shuffle_epi32(_mm_cvtsi32_si128(0x3030303u), 0), _mm_srli_epi16(v79, 6u)),
v80));
*(__m128i *)&s1[v6] = _mm_xor_si128(
_mm_or_si128(_mm_add_epi8(v86, v86), _mm_and_si128(_mm_srli_epi16(v79, 7u), v80)),
_mm_shuffle_epi32(_mm_cvtsi32_si128(0xAAAAAAAA), 0));
v6 += 16LL;
}
while ( v6 != 32 );
LOBYTE(v87) = v106;
v88 = v5[v106];
if ( (v88 & 0x400) != 0 )
{
if ( (v88 & 0x100) != 0 )
v87 = (v106 - 64) % 26 + 65;
else
v87 = (v106 - 96) % 26 + 97;
}
s1[32] = ((2
* ((2
* ((2
* ((2 * ((2 * ((2 * ((2 * v87) & 2 | ((v87 & 2) != 0))) | ((v87 & 4) != 0))) | ((v87 & 8) != 0))) | ((v87 & 0x10) != 0))) | ((v87 & 0x20) != 0))) | ((v87 & 0x40) != 0))) | ((unsigned __int8)v87 >> 7)) ^ 0xAA;
LOBYTE(v87) = v107;
v89 = v5[v107];
if ( (v89 & 0x400) != 0 )
{
if ( (v89 & 0x100) != 0 )
v87 = (v107 - 64) % 26 + 65;
else
v87 = (v107 - 96) % 26 + 97;
}
s1[33] = ((2
* ((2
* ((2
* ((2 * ((2 * ((2 * (((v87 & 2) != 0) | (2 * v87) & 2)) | ((v87 & 4) != 0))) | ((v87 & 8) != 0))) | ((v87 & 0x10) != 0))) | ((v87 & 0x20) != 0))) | ((v87 & 0x40) != 0))) | ((unsigned __int8)v87 >> 7)) ^ 0xAA;
if ( !memcmp(s1, s2, 0x22uLL) )
puts("Congratulations knight!");
else
LABEL_5:
puts("Incorrect flag!");
return 0LL;
}代码几百行,而且这指令集导致代码混淆很严重,分析难度挺高的,能知道的代码逻辑就是flag的长度为34,并且最后与s2进行对比。前32个字节怎么加密很难看得懂,分析也感觉不现实。
但是这里的最后两个字节则很明显是单独加密,先将某个数据转化为字母,然后进行加密。
不过我们调试其实可以发现代码的加密都是单字节的加密,比如对于这里的前16个字节我们都输入1,后16个字节都输入2,也就是11111111111111112222222222222222
得到加密后的输出如图
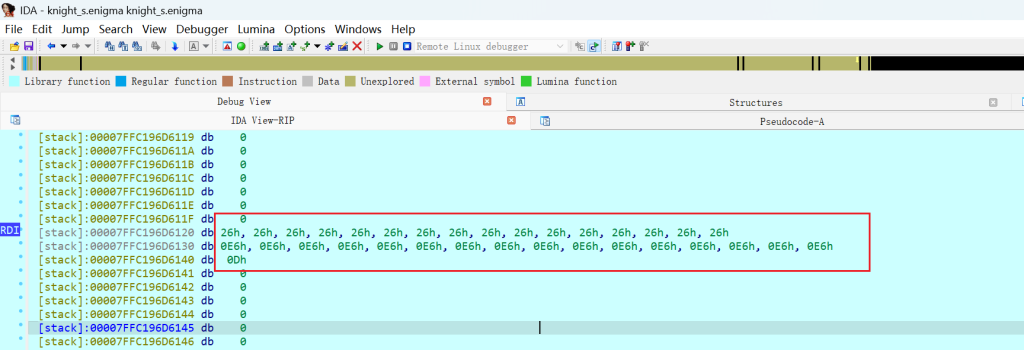
当然你也可以通过其他方式去验证整个程序是进行一个单字节的加密,这就给了我们一个爆破的空间。
最简单最笨的,可以直接手动输入所有的字母、特殊字符和数字,得到一个加密的映射表,然后和密文比对逆向来得到flag。
这里学习直接使用Pwntools来爆破,值得学习的一个方法。这里参考的是虾饺一个大哥的做法,挺灵活的,它首先把二进制程序最后的判断处
if ( !memcmp(s1, s2, 0x22uLL) )改成了
if ( !puts(s1) )也就是在最后把程序加密后的结果输出,然后再在Python脚本中逐个字节判断是否正确来进行爆破,Python的解题脚本如下
from pwn import * # 导入pwntools库,用于与二进制程序进行交互
# 初始化flag,长度为34个字符,全部为'a'
t = "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"
# 这是预期的输出字节数组,长度为34
ans = [0x98, 0x88, 0x98, 0x48, 0x74, 0x50, 0x8c, 0xa6, 0x5c, 0xbc, 0x64, 0xec, 0x04, 0x06, 0x50, 0x9c, 0x5c, 0xfc, 0xbc, 0x3c, 0x04, 0x50, 0xf4, 0xa6, 0xc4, 0x50, 0xbc, 0xa6, 0x04, 0x50, 0x26, 0x04, 0x50, 0x14]
# 遍历字符串t的每一个字符位置(0到33)
for k in range(34):
# 遍历所有可打印的ASCII字符(0x21到0x7F)
for i in range(0x21, 0x7F):
# 将字符串t的第k个字符替换为当前尝试的字符i
t = t[:k] + chr(i) + t[(k+1):]
# 启动目标程序("./knight_s.enigma_fix")的进程
p = process("./knight_s.enigma_fix")
# 将修改后的字符串t发送给目标程序
p.sendline(t.encode())
# 读取程序的输出,`readrepeat(1)`表示读取1秒内的所有输出,不会读取我们的输入
rec = p.readrepeat(1)
# 关闭进程
p.close()
# 从输出中提取关键部分,假设输出的第二行包含"secret: ",我们取该部分
terms = rec.split(b"\n")[1].split(b"secret: ")[1]
# 检查terms的长度是否大于k,并且terms的第k个字节是否与ans的第k个字节匹配
if len(terms) > k and terms[k] == ans[k]:
# 如果匹配,打印当前的字符串t,并跳出内层循环,继续下一个字符的猜测
print(t
break
#KCKF{_c0ngrat5_knight_y0u_g0t_1t_}
t = t[:2]+"T"+t[3:]
#这里因为爆破出的flag第三个字节不正确,需要纠正
print(t)
#KCTF{_c0ngrat5_knight_y0u_g0t_1t_}这里将memcmp函数调用修改为puts,直接在IDA的Assemble选项就行
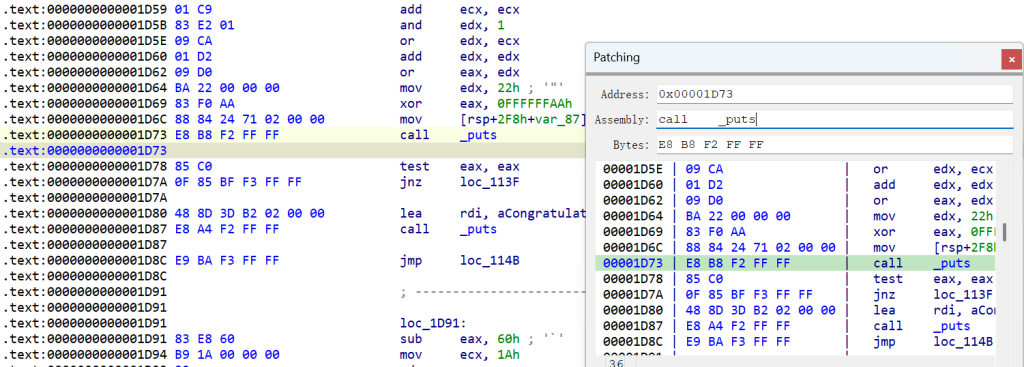
也可以自己算地址偏移,改opcode。
这里没有修改传入函数的参数,但是刚好能puts加密后的结果,如果遇到传入函数的参数不如我们所愿的话,可能就要再修改传参的汇编指令了。
所以题目的flag就是KCTF{_c0ngrat5_knight_y0u_g0t_1t_}